Welcome to my HACKvent CTF competition write-up! I was fortunate enough to participate in this annual event for the seventh year. Each day in the lead-up to Christmas, a new cybersecurity challenge was released, testing my technical skills, problem-solving abilities, and time management as the challenges got progressively harder. Total points were only awarded to those who could solve the challenges within 24 hours – the last three challenges in the category “leet” within 48 hours.
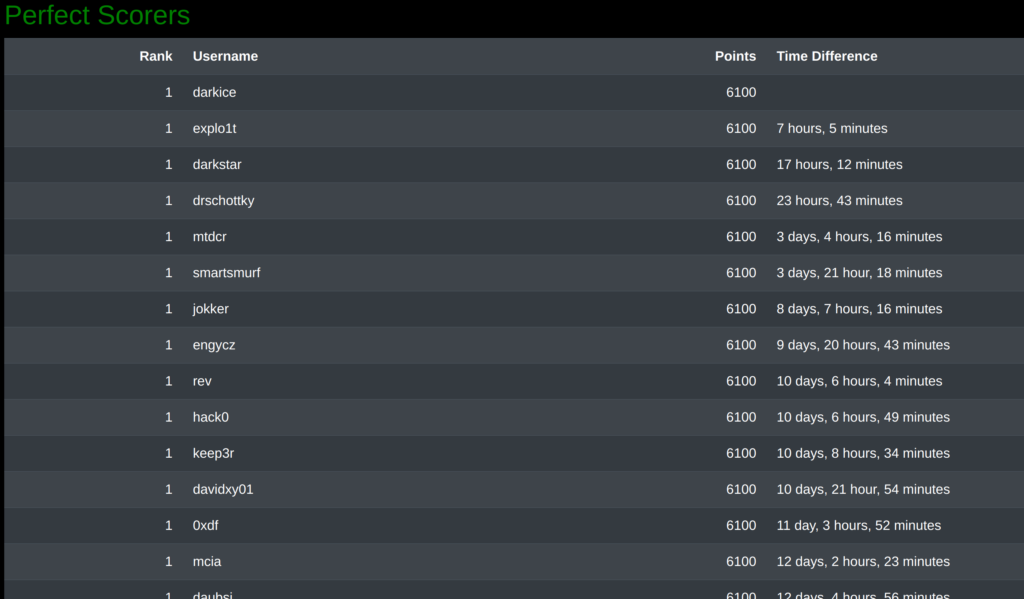
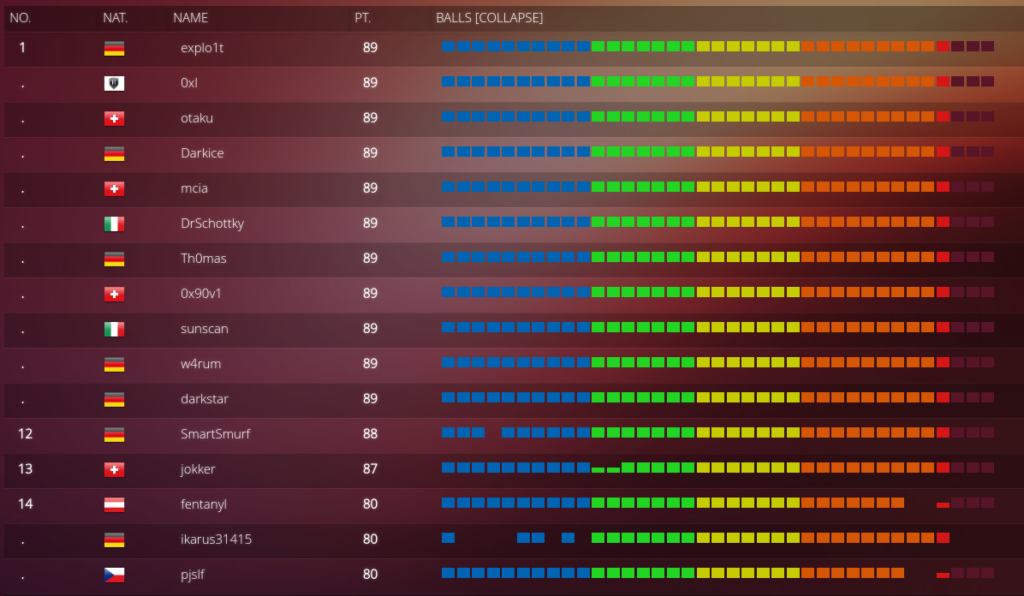
I am thrilled to share that I solved 24 of the 25 challenges and 23 within the requested time frame this year, earning most of the points available. I completely skipped the challenge on day 24, as after 30 hours, nobody solved it, and I had yet to start with it. It was too much effort to tackle during the busy holiday season.
I want to extend a big thank you to all of the challenge authors, Compass Security, and especially Kuyaya, for his hard work in organizing this event and involving the participants in the decision-making process. I also want to thank my family and friends for their patience and understanding during the competition. I am excited to share my journey through this year’s competition with you, and I hope you enjoy reading my write-ups and learning from my experience.
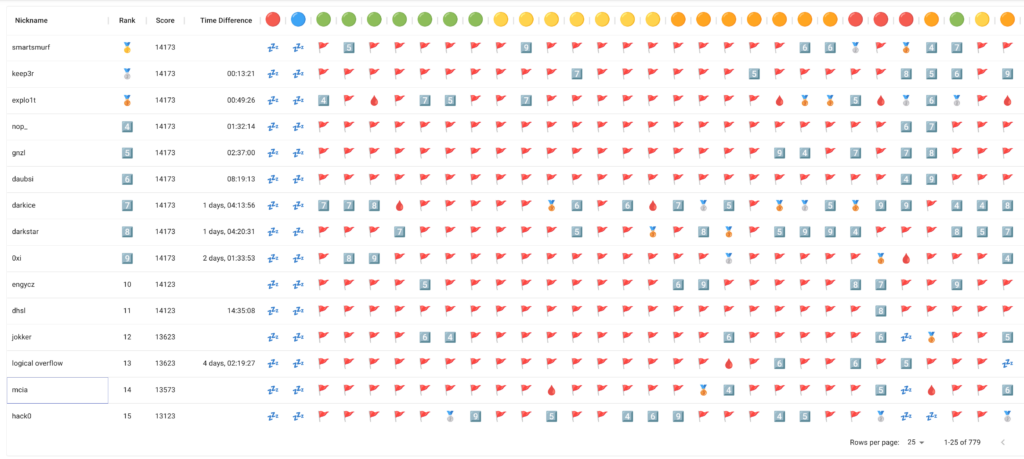
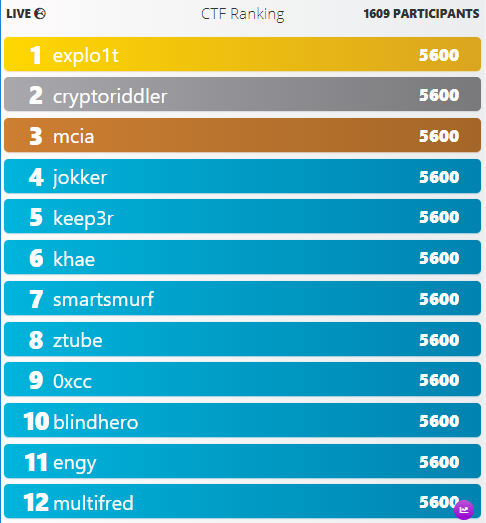
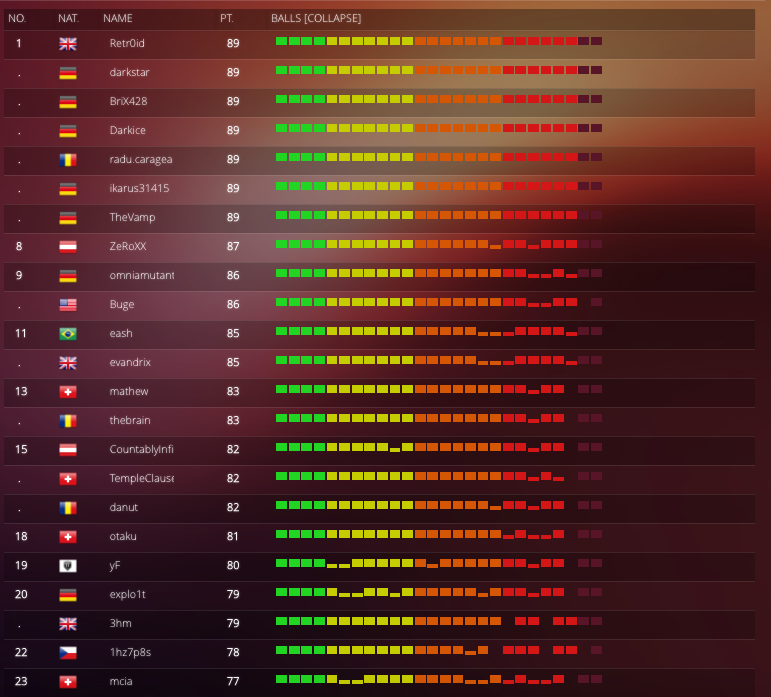
When writing this blog post, I was first in the ranking as I was the only one who had solved the surprise challenge of day 25 till then.
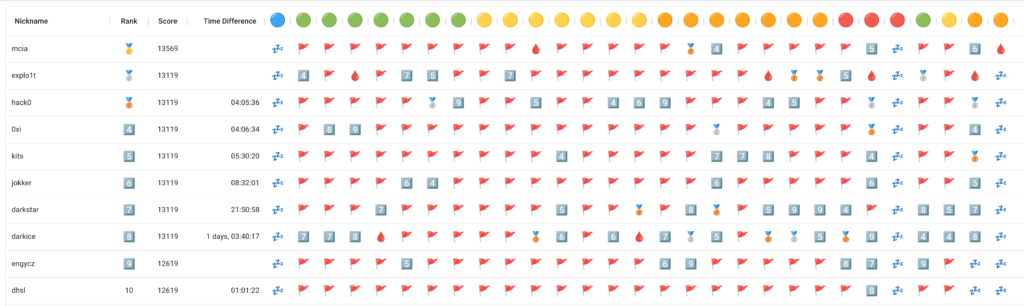
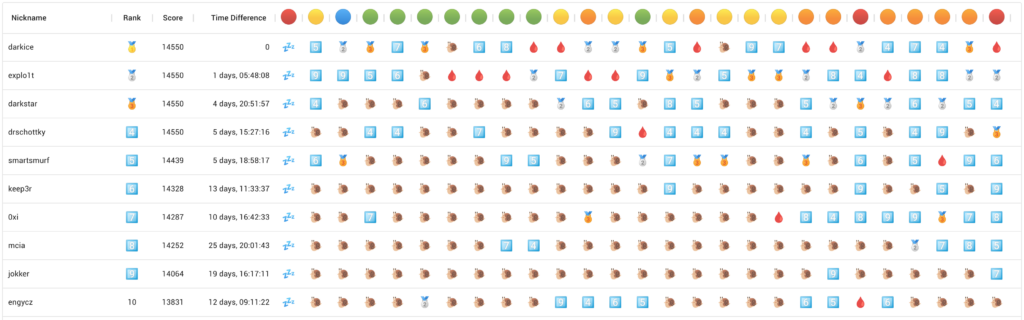
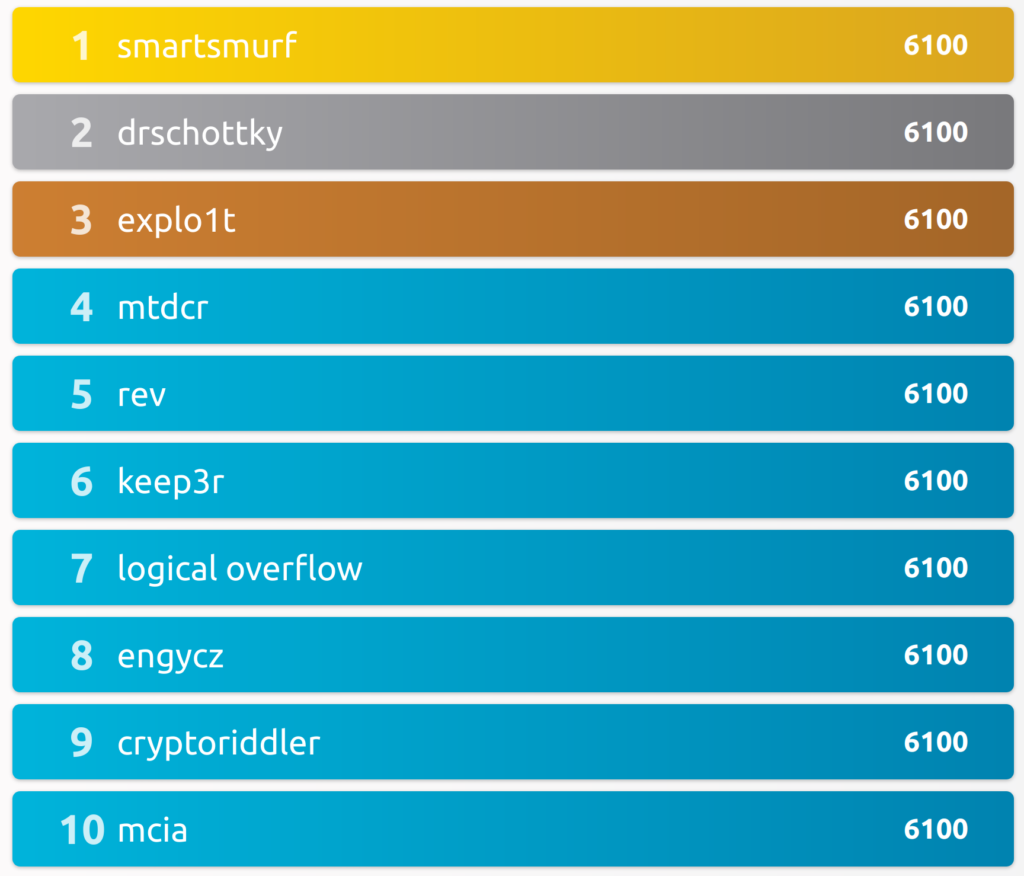
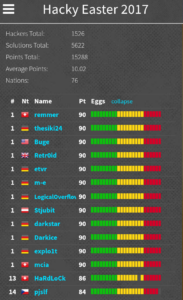
Of course, this changed until the end of the competition, as other participants solved all the challenges in time. In the final ranking on the 31st of December 2022, I ended up in place #14.